PHPENV has added the support of haproxy.yml. If you have an external IP and domain name, you want to get HAProxy and certificate application
It should be quite simple through deviny/phpenv.
In this article, let us see how to use HAProxy in the HAProxy environment setting in PHPENV.
Practical operation, you can also check out my YouTube Note:
In the phpenv directory, the content of the haproxy.yml file is as follows:
version: '3.6'
services:
haproxy:
build:
context: ./dockerfiles
dockerfile: Dockerfile-haproxy
image: ${PROJECT}_haproxy
ports:
- ${HTTP_PORT-80}:80
- ${HTTPS_PORT-443}:443
volumes:
- ./etc/haproxy:/etc/haproxy
- ./etc/haproxy/proxy.pem:/etc/ssl/phpenv/proxy.pem
- ./etc/ssl:/etc/letsencrypt
#-f <configuration file|dir>
#command: /usr/local/sbin/haproxy -f /etc/haproxy -d
networks:
- dlaravel_net
networks:
dlaravel_net:
As you can see in this file, he will go to build, Dockerfile-haproxy under the dockerfiles directory, why use HAProxy, because its reload speed is super fast,
The user will hardly notice the change of the certificate, His function is really easy to use, different ACLs can lead to different hosts, and it is extremely stable.
In the HAProxy setting of phpenv, all .well-known/acme-challenge will hit the backend port 8080 of the local side.
Through this mechanism, we can allow all HAProxy backend hosts to apply for Let's encrypt certificates without creating folders.
The HAProxy environment configuration file in phpenv is very simple. We can customize the name and put it in the envs folder. The content is as follows, and the PROJECT name can be set according to our own preferences.
DEFAULT=haproxy
PROJECT=ha
HTTP_PORT=80
HTTPS_PORT=443In the above settings, DEFAULT= is specified, which means that when phpenv links to this configuration file, it will use haproxy.yml in the directory as its default YAML file.
So the first step, when we have created the PHPENV environment configuration file in envs, we can execute ./link once to link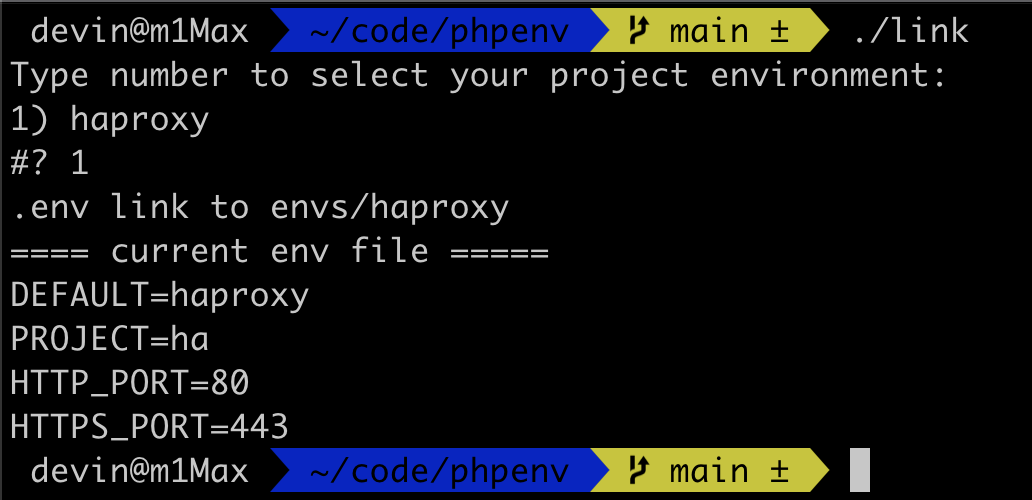
In the second step, the image of the Build environment only needs to be executed once in the new environment. 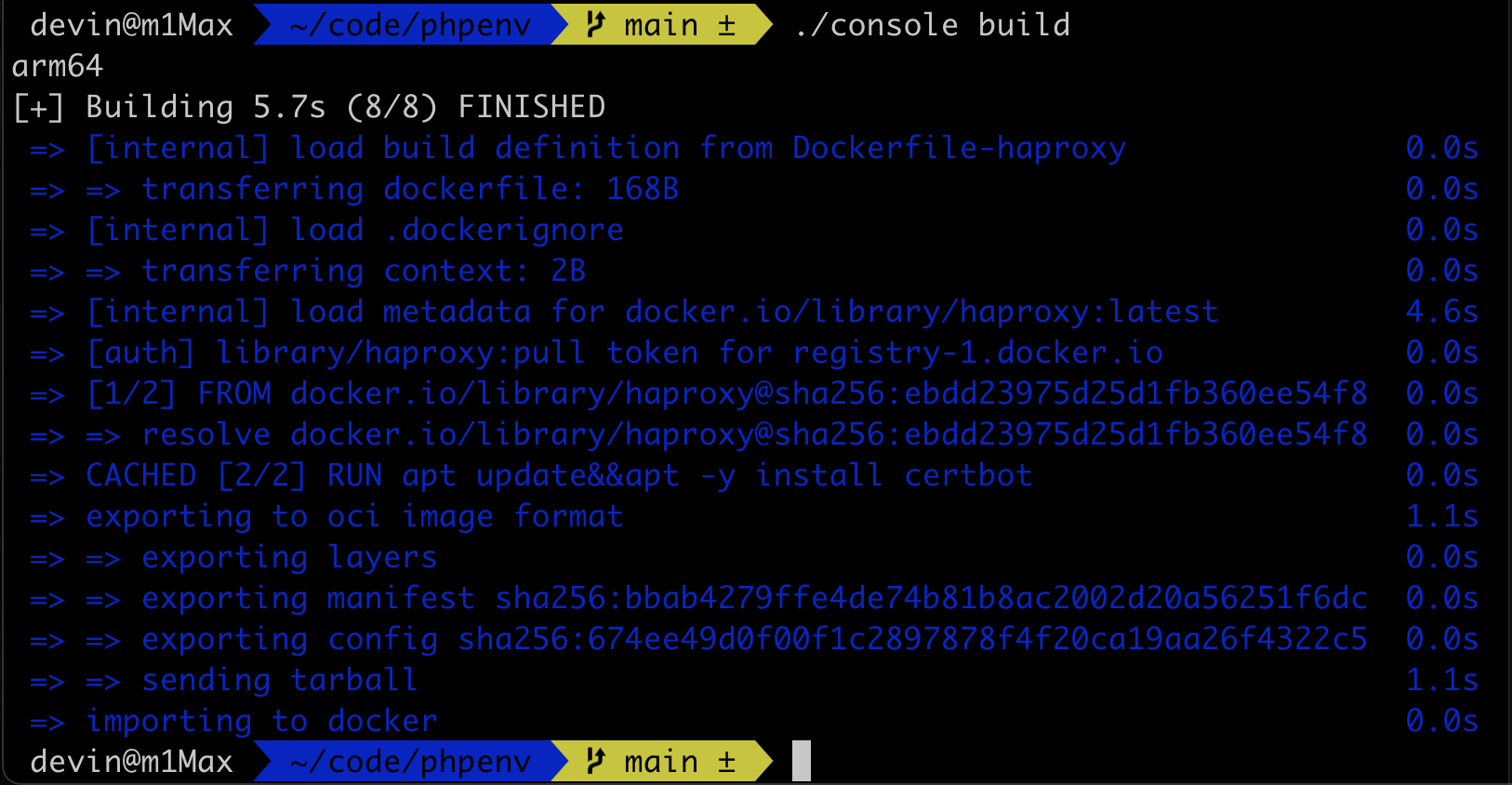
Third Let’s start it and see it
We can start it through ./start and stop it through ./stop, and then check the startup status through ./console ps.
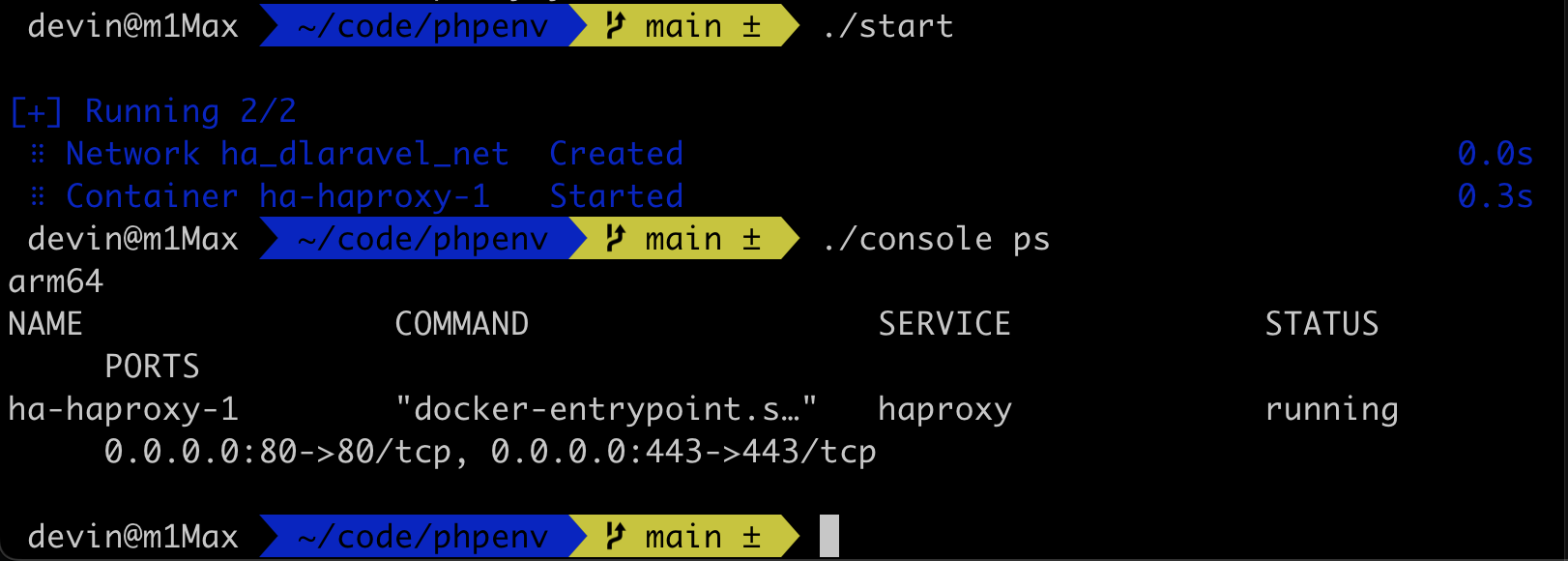
./console upIn the case that we have no certificate at all, we can enter the container and execute the following command to obtain a free SSL certificate
The following command can enter the HAProxy container
./console exec haproxy bashAfter entering the container, you can use the following command to apply for a certificate
certbot certonly --standalone --http-01-port 8080 --email devin@ccc.tc \
--dry-run \
--agree-tos --preferred-challenges http \
-d <your domain>The above --dry-run can be tested first. After confirming that there is no problem, remove --dry-run and run officially. If it fails too many times, it will be locked and will not be applied for.
We can copy the environment settings of the backend host through phpenv.cfg.example for adjustment and modification, and become phpenv.cfg. 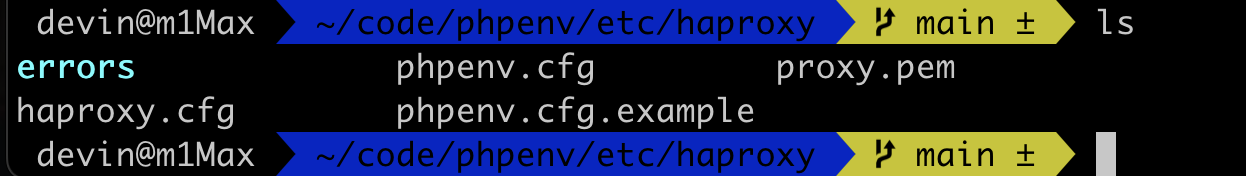
in phpenv The backend must have a certificate file. If you use let's encrypt, you can combine fullchain.pem and privkey.pem into one file and save it as proxy.pem.
frontend phpenv
mode http
bind :443 ssl crt /etc/haproxy/proxy.pem alpn h2
option forwardfor header X-Real-IP
http-request add-header X-Real-IP %[src]
http-request add-header X-Forwarded-For %[src]
acl acme path_beg -i /.well-known/acme-challenge
redirect scheme https code 301 if !{ ssl_fc } !acme
acl SUBDOMAIN_url hdr_beg(host) -i SUBDOMAIN.duckdns.org
use_backend SUBDOMAIN_server if SUBDOMAIN_url
backend SUBDOMAIN_server
mode http
fullconn 10000
cookie SITEID insert indirect nocache
server SUBDOMAIN host.docker.internal:1050
In the above example, we can have many acls with use_backend and backend, leading to different backends.
If necessary, you can also have multiple certificate files at the same time.
ind :443 ssl crt /etc/ssl/ccc.tc/ccc.tc.pem alpn h2,http/1.1 crt /etc/ssl/ccc.tc/demo.ccc.tc.pem alpn h2,http/1.1 crt /etc/ssl/ccc.tc/e-course.app.pem alpn h2,http/1.1
About the settings of multiple ACLs and backends, it looks like this:
frontend phpenv
mode http
bind :443 ssl crt /etc/haproxy/proxy.pem alpn h2
option forwardfor header X-Real-IP
http-request add-header X-Real-IP %[src]
http-request add-header X-Forwarded-For %[src]
acl acme path_beg -i /.well-known/acme-challenge
redirect scheme https code 301 if !{ ssl_fc } !acme
acl a_url hdr_beg(host) -i aaa.ccc.tc
acl b_url hdr_beg(host) -i bbb.ccc.tc
use_backend a_server if a_url
use_backend b_server if b_url
#BACKEND A
backend a_server
mode http
fullconn 10000
cookie SITEID insert indirect nocache
server demo3tc-a host.docker.internal:1050
#BACKEND B
backend b_server
mode http
fullconn 10000
cookie SITEID insert indirect nocache
server demo3tc-a host.docker.internal:1051
By the way, phpenv can also perform tcp mapping, for example, as follows:
listen vscode
bind *:8444
option tcplog
mode tcp
acl network_allowed src 211.72.111.145 111.248.102.24
tcp-request connection reject if !network_allowed
server sagent 192.168.99.123:1443
The above are some environmental descriptions of phpenv's HAProxy, and I will add it when I have the opportunity. 😁




No Comment
Post your comment